With 1 million Android mobile devices infected in India, is your mobile safe?
In a mobile security report by Cheetah Mobile, the company claimed that in 2015 as many as a million Android mobile devices were infected in India. The report was perceived from a data base of 567 million global monthly active users and an installation base of almost two billion users using Cheetah Mobile’s utility applications.

According to Visual Networking Index study by Cisco, India is the second largest smartphone market globally. In India, there were 590.3 million (47 per cent of India's population) mobile users in 2014, up 18 per cent from 500 million (40 per cent of India's population) in 2013. Thus, this makes India the second most infected country after China in terms of viruses too, owing to the large Android user base and third-party app markets, as claimed by the Cheetah Mobile report.
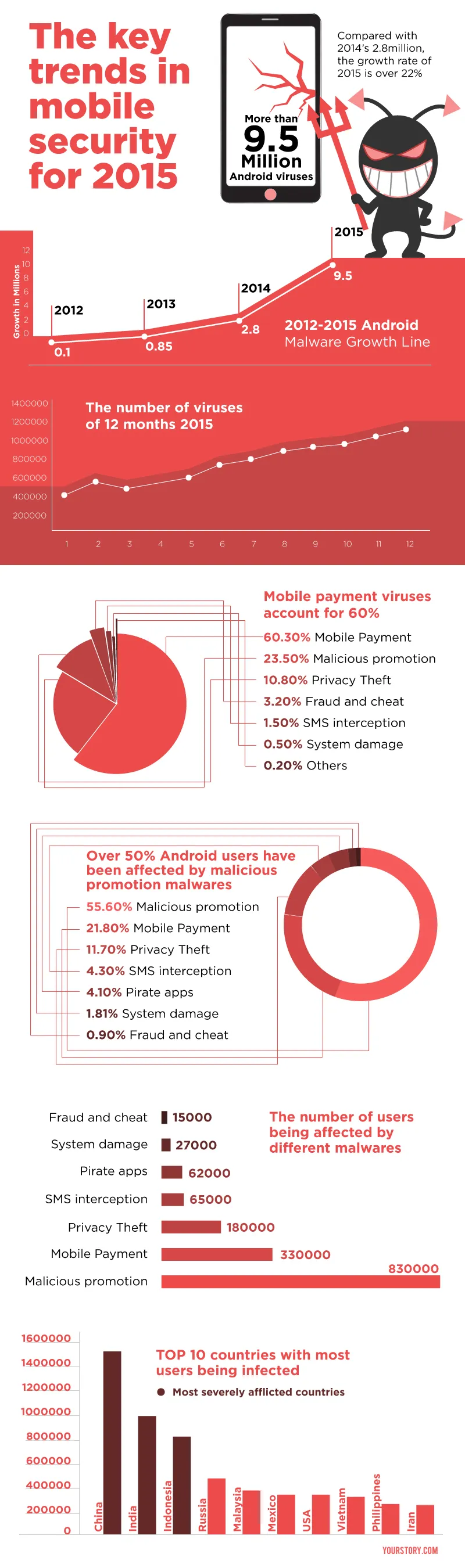
While one million seems to be a small number in the face of the total number of smartphone users in India, what one should focus on is the rising number of Android viruses which, according to the survey, has exceeded 9.5 million, as opposed to the 2.8 million in 2014. This is a growth rate of over 22 per cent.
Bhanu Prakash Valluri, Vice President- Product, App Vigil thinks the threat might be larger. He believes that one million is just the number of devices reported. He believes there may be much more service malware under the blanket, taking the estimate much higher.
This is especially a point of concern as, according to a report by IAMAI and market research firm IMRB International, the number of local language Internet users is 127 million as of June 2015 and is growing at 47 per cent year on year, owing to the increasing use of smartphones in rural areas of the country.
According to Bhanu, the non-tech-savvy mobile users or the first-time smartphone users can be a major challenge to address when it comes to mobile security.
“E-commerce companies can be a wet blanket on that front as they entice these first-time users, (where they see a big potential market) through promotional discounts. This inculcates in them a behaviour of tapping on promotional pop-ups, which tends to follow through for other promotion malware, ” he adds.
According to the Cheetah Mobile report, more than 55 per cent Android users have been affected by malicious promotion malware, popping up either as advertisements or forced installations of unwanted apps. Privacy theft Trojan is a common one amongst these malware, which hides in mobile users to steal text messages, contact information, location and personal photos.
The report also quotes that 60 per cent of the 9.5 million Android viruses is related to mobile payments. The report quotes that mobile payment malware can be disguised as normal payment pages enticing users to enter personal information, ID information, bank account information, and phone number.
As many as over eight lakh Android users were affected by malicious promotion malware, while mobile payment viruses cost information loss to more than three lakh users.
Morality of the ecosystem
Bhanu believes that the focus should ideally be on deploying secure apps. Security should be not seen as a luxury but an essentiality. While developing an app, security should be as high as functionality.
This is because newer APIs are being introduced by developers almost every day increasing the attack surface area for malware. Moreover, the trust placed on smartphones has gone up drastically with users using them to transact and pay for big-ticket items.
Bhanu adds that the morality in the ecosystem has increased where the apps developed are asking for more permissions rather than just asking for a list of them in one go before installations. Also, apps are built in a way where you can just manually feed inputs (in case of taxi apps) rather than give away critical information.
However, there is a need to take private information more seriously by having more policy changes. Publishers should be transparent about what information is being utilised from the user before installation. Moreover, it is technically possible and executed by policy that an app can’t be published if it doesn’t justify its permissions.
Critical vulnerabilities
In 2015, following were the top vulnerabilities which took centre stage, according to the report:
- Stagefright: This contributes to 95 per cent of the Android users running version 2.2 to 5.1, vulnerable to hackers wanting to take control over user’s phones. This resides in a core Android component called 'Stagefright,' a multimedia playback library used by Android to process, record and play multimedia files.
- Homescreen applications: CM Security Research Lab discovered in May 2015 that homescreen applications might contain potential threats. These apps create and present fake messages to the user for viewing which put the users under risk.
- Certi-gate: Essentially, this includes a set of flaws between mobile Remote Support Tool (mRST) used by Android device manufacturer and network service provider. This allows free access to the device by hackers to initiate actions like screen shoot, keyboard records, and privacy stealing and front-door access. The latest version, Lollipop, which is believed to be the most secure version, can also be struck by this.
- GHOST: Affecting Linux systems, attackers use this flaw to gain system privileges, which means the data we use frequently and store on web pages can easily be stolen. This can also be used by hackers to secretly implant viruses on sites.
- Freak attack: This renders users of browsers vulnerable to interception of their electronic communication while browsing and visiting hundreds of thousands of websites.
Following is an infographic depicting more facts on the mobile security concerns: