

Biometrics for Aadhaar Authentication in Government Schemes
Biometric Technology – Assisting Government To Efficiently Implement Social Welfare Schemes
- : Leading the nation towards digital inclusion & empowering common Indians.
- Aadhaar is one of the key elements in India’s move towards a cashless economy.
- Biometric technology helps to reduce duplicate and ghost entries in the list of beneficiaries of government schemes, and pave the way for direct benefit transfers.
Since the inception of the world's largest citizen biometric identification program – Aadhaar, the Indian Biometrics Market has noticed a substantial growth, reaching up to US$ 1.7 Billion by the end of 2018, as per the IMARC market research reports.
Biometrics has already become a standard feature of identification and authentication in multiple countries across the globe. There are some 195 countries in the world today, out of which around 160 countries (covering 80 percent of the nations) have mandated the national ID cards. Out of these hundred and sixty countries, nearly 10 percent of them have implemented biometric authentication for carrying out the process of citizen identification.
Countries like Canada, India, France, US, UK, Germany, Italy, China, and many more have given stimulus to the biometric industry in the recent years by applying biometric technology in diversified domains to the make system more secure, fast and reliable.
Biometric identification is the process by which individuals are identified using their distinctive physiological characteristics such as fingerprint, IRIS, face and palm vein. Consequently, biometric technology is on the growth trajectory since a couple of years in India as it makes the presence of a person obligatory while carrying out mainstream identification and authentication practices.
The three steps involved in biometric authentication
The heart of biometrics is a biometric sensor which captures the physiological traits of an individual and converts them into a mathematical representation. Biometric authentication is a three-step process: Capture, Process and Enroll, followed by a Verification or Identification process.
- In the capture process, a biometric device captures raw biometric data by fingerprint or IRIS scanner in the form of an image.
- In the second stage of processing, it extracts the distinguishing characteristics from the raw biometric data and converts into a biometric template (a mathematical representation of biometric data).
- Next stage is the process of enrollment. In this biometric template is stored / registered in a database for future comparison during authentication.
There are mainly three types of biometric fingerprint sensors - optical, capacitive and ultrasonic sensors. With the increasing adaption of biometric technology, optical fingerprint recognition is considered as one of the most favored biometric modalities to identify/verify the identity of a person.
Aadhaar – A driving force behind implementation of Biometrics in India
The Indian Government floats a myriad of social welfare schemes to benefit and uplift the weaker sections of society. With the proliferation of UIDAI's unique Aadhaar-based biometric identification program, the government ensures the reduction of de-duplication and authentic supply of services.
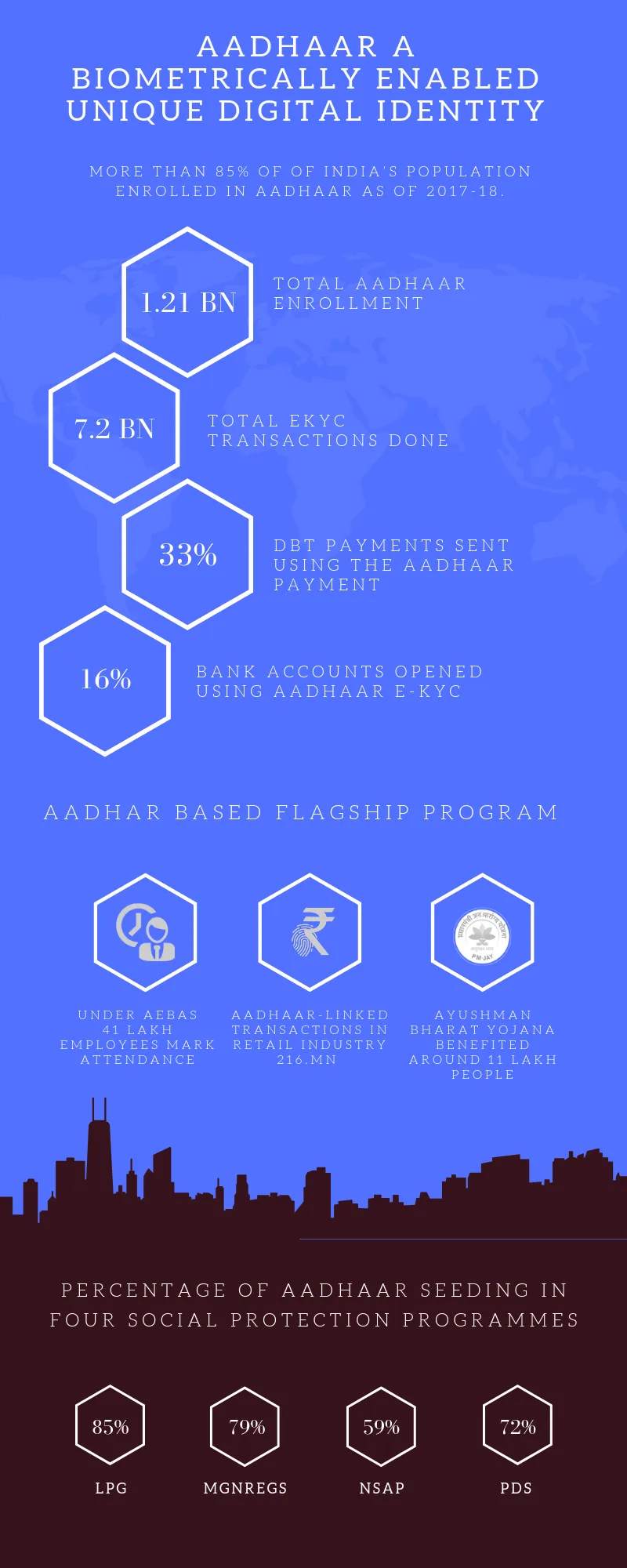
The Aadhaar program proffered a biometrically enabled unique digital identity - Aadhaar number to more than 1.2 billion Indian citizens as of February 2019.
GOI through Aadhaar ID card bestows a flawless approach to efficiently run various government flagship programs and encourage fair delivery of benefits to the needful class, including employment guarantees, direct benefit transfer, food subsidies, etc.
Since the adaption of Aadhaar in 2009, UIDAI has developed a state-of-the-art operational and technological structure to enroll and identify the citizens utilizing innovative biometric devices. Biometric technology has become the cornerstone of several social welfare schemes in India for promoting timely delivery of the objectives in a reliable, efficient and unprejudiced manner.
According to the 2016-2017 ‘State of Aadhaar’ reports, databases of four major social welfare schemes seeded around 74 percent beneficiaries by Aadhaar in 2017.
Also, 33 percent of beneficiary got the benefit of subsidies through direct benefit transfers (DBT) using Aadhaar based electronic payments transfer in their bank account during the fiscal year 2016-2017.
Now, in India individuals can easily be able to prove their identity securely through biometric devices.
The government is now digitally linking public services/schemes with Aadhaar and biometrics to increase transparency along with efficiency in functioning & monitoring of social welfare schemes, says Mr. Hiren Bhandari (Technical Director of Mantra Softech India Pvt. Ltd).
Aadhaar authentication ecosystem
The Aadhaar database allows government & private sector entities to authenticate the users with their Aadhaar records. Aadhaar Authentication Ecosystem is a process by which a person’s Aadhaar number, along with demographic or biometric information, is sent to CIDR (Central Identities Data Repository) for verification.
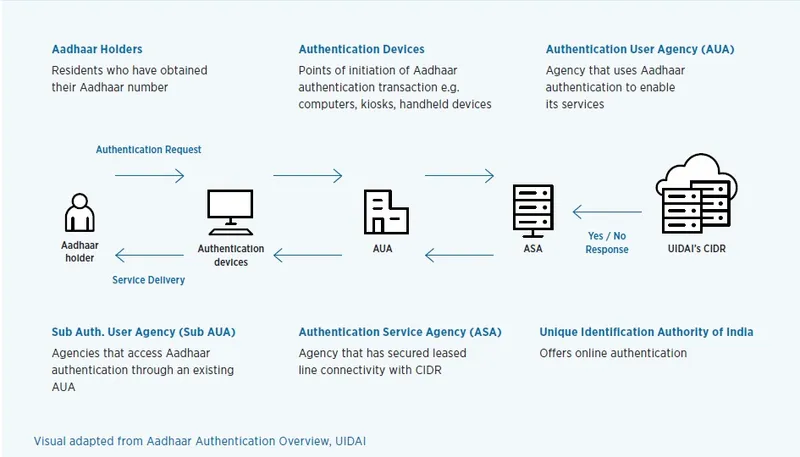
- An Aadhaar holder’s biometric data is captured using biometric authentication devices such as fingerprint or iris scanners.
- The biometric information of the user will further be sent to the Authentication User Agencies (for instance the state government) to gain access to the Aadhaar authentication facility.
- The data is further transferred to the Authentication Service Agency (ASA) to connect to the CIDR and transmit authentication requests from AUAs to the CIDR.
- In turn, they transmit the CIDR’s responses to authentication requests back to AUAs.
- Finally, UIDAI’s CIDR will match the biometric pattern of the user with the database and send a Yes/No response to the authentication.
Secure biometric device architecture
Identification and authentication of individuals via biometric devices will involve a few steps:
- When a biometric device is connected with the Client Service authentication app, it sends an encrypted key to the HSM server which provides the encrypted sign to activate the device. These biometric devices are known as registered devices or RD service-enabled devices.
- The biometric device will capture the fingerprint, iris or facial images of the user, encrypt the biometric data and send it to the client service authentication application.
- Next, the encrypted data will be sent to UIDAI's server that will decrypt the biometric data of a user to match it with the Aadhaar database.
- Based on the data matching process of the server, UIDAI’s server will generate a ‘success/failure’ result.
Merits of seeding Aadhaar and Biometrics with Government-led Initiatives
The Aadhaar-linked biometric identification infrastructure allows the delivery of welfare services to the intended beneficiaries and reduces the leakages. The ease and convenience of biometric authentication assist the Central and State Government in implementing transparent, fair and effective services to the beneficiaries.
"We were able to weed out bogus and duplicate beneficiaries by using Aadhaar," J Satyanarayana, chairman of the Unique Identification Authority of India (UIDAI) said in a program at Indian School of Business (ISB).
Some of the most significant objectives of Aadhaar enabled biometric identification process are: permitting the beneficiary to avail government subsidies efficiently, assisting the citizens in opening a bank account, offering financial and banking services to the people residing in rural or semi-rural areas, disbursing provident funds directly to the account of a holder and much more.
The featured merits of biometric technology to the Aadhaar program are:
- Increases transparency – It is easy to monitor the fund utilization of the social welfare schemes from the state level to the individual beneficiary.
- Low identification cost – The Identification of the beneficiary for the social welfare scheme in the traditional enrollment process costs between 200 INR to 400 INR per enrollment whereas a Biometric enrollment costs between 25 INR to 40 INR per enrollment which is quite cost-effective.
- Less time consuming to implement a scheme – The process of verifying the beneficiary’s Identity documents is a lengthy process because it utilizes a lot of man hours. Verification through biometric eKYC & OTP is quite hassle free and saves time in implementing social schemes.
- Scalable – Due to the high operational efficiency of this advanced technology, the Govt. schemes can be easily scaled up without incurring a similar proportion of cost (Manpower and Machinery) irrespective of an increasing number of beneficiary for social welfare scheme.
- Easy to monitor the effectiveness of scheme – It involves real-time monitoring of the welfare scheme and keeping a track of the bottlenecks in the entire program.
Security risks and challenges
- Security Level – The risk of unauthorized access to Aadhaar’s database is always prevailing, leading to a high level of security threat.
- Increasing Cost – Biometric fingerprint authentication is the most common method of identifying a beneficiary. However, compared to the fingerprint recognition, the iris recognition proffers a higher level of accuracy and security. But, employing iris scanner devices to enhance security will increase the cost of the project as iris sensors are quite expensive compared to fingerprint sensors.
- Loss of Data – The recovery time and backup mechanism of the Aadhaar project database may prove to be a significant challenge in the case of the technical or natural failure.
The way forward
Currently, it is pretty essential to address two issues on a priority: Privacy and Security. There is a distinct possibility of citizens' Aadhaar details being leaked or misused, including their Biometric information. Aadhaar is suspect to profiling and surveillance; therefore it is the duty of the State to be transparent to its citizens.
Right now, there are no laws to protect and deliver justice to people whose identities have either been compromised. Hence, there is a need to formulate provisions that not only compensate but also protect citizens against leakage of their distinctive personal information and severely punishing those found guilty. Aadhaar details/information of individuals must be shared only if mandated by a judicial body such as a Court or a Quasi-Judicial body made of eminent members in accordance with the legal framework.
Following the Supreme Court’s judgment, now the ground rule of privacy is efficiently laid out. Although it is equally essential to record that under the threat of privacy, one cannot abandon the biometric technology. Artificial intelligence and IoT holds immense potential to use the Aadhaar database for efficiently implementing the social welfare schemes in the near future.
However, it is substantial to reiterate that the Aadhaar ecosystem is extremely safe and uses best practices with regards to the safety and security of citizen's vital biometrics data. To mitigate the concerns of residents, the UIDAI has lately added another layer of security by presenting the option of Virtual ID for those who do not desire to disclose or render their Aadhaar numbers.







