

Worried About Mobile App Security? Have A Look At The Checklist To Follow
Mobile app security has become a major concern for businesses. No matter how good for your app is, if security is breached it spells great troubles. In order to provide a solution to this menace, developers all over the world are working. Here is a checklist to follow to avoid security breaches.
Facebook’s WhatsApp informed a “serious security vulnerability” on its platform on 14th May’2019 to the company’s lead regulator in the EU, Data Protection Commission of Ireland. This shocked its 1.5 billion monthly users.
WhatsApp’s confirmation about the security flaw in its application has brought the popular messaging tool under suspicion. The application which was once known for the high-level security of its well-known end-to-end encryption policy is under scrutiny.
You will be shocked to know that WhatsApp is not alone in this boat! The top-notch application platform, iOS entered the top news last month with similar security flaws.
An app was discovered in April’ 2019 which was spying on Apple App store’s users and bypassed Apple’s security. The platform which was once considered more secure than Google Play has unveiled its non-secure attributes.
This has made 2.71 billion smartphone users wonder if their apps are really simple and secure! In turn, this is bringing smaller brands on their feet to look into the app’s security to provide a more satisfactory user experience to their customers.
Every organization, from startups to fortune 500 companies are going digital with their own mobile applications. This provides them quick and consistent connectivity with their customers.
Although there is cutthroat competition in the mobile app industry, so it is not easy to make your app outshine others. There is an ever-growing demand for mobile applications with a total download to reach 352.9 billion in 2021, according to a report by App Annie. Here is a graphical representation to their report:
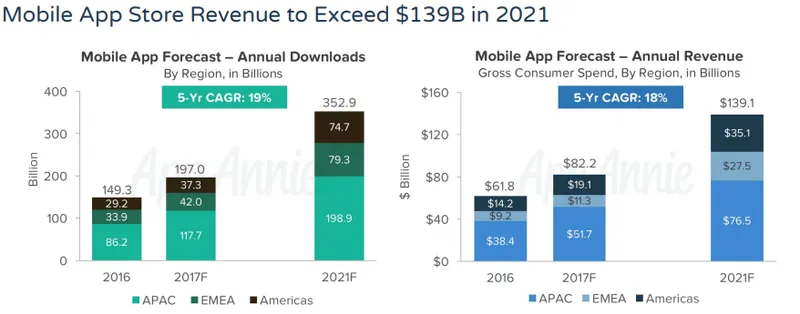
So, it is obvious that companies investing in mobile applications will fear security issues. They are looking for high-end solutions to make their applications more secure.
To help such businesses, we have researched and found out the major areas of security concerns for mobile applications. You can follow these mobile apps security checklist given below to make your applications more safe from cyber crimes.
Mobile app security checklist for 2019:
- Secure source code: The most important one

You must be aware of the recent security mistake in Samsung’s smart home ecosystem, SmartThings. The bug has exposed Samsung apps, projects and services to the public and it was first found out by a security researcher Mossab Hussein on 10 April’ 2019.
Samsung has failed to secure its projects with passwords and its source code of the Android SmartThings app was available. With this discovery, Hussein got access to 45-135 private as well as public accounts.
So, undoubtedly, securing the source code is the most vital aspect of mobile application development. Letting the source code accessible to hackers is like leaving your house unlocked!
If the projects, like in the case of Samsung, are left without a password, anyone will be able to view, download and change the source code. So, what you are required to do?
2. Cryptography: Make sure it is not broken
Problems in encryption can pose serious issues in the security of a mobile application. Strong encryption with appropriate implementation is highly crucial. Broken cryptography happens when you have weak encryption algorithms.
Another case of broken cryptography can occur when an improper implementation of strong encryption is conducted. Sometimes, in order to speed up the process of development, iOS or Android app developers use certain encryption algorithms that can motivate attackers to crack passwords.
Another issue may arise when with strong encryption algorithms there are flaws in the code. This is because in such cases the attackers will not require passwords to gain access and will be able to harm the app's high-end functions.
3.Transit encryption: Vital to protect high-risk data
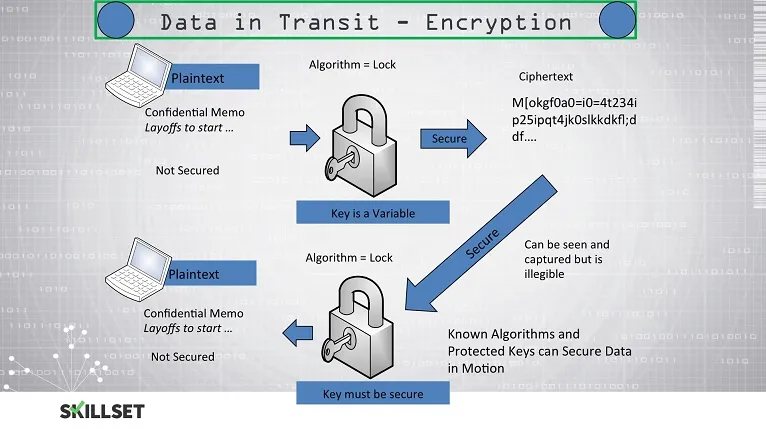
When data is transferred, it is exposed to various risks. Some sensitive data like passwords, API keys and username are subject to the higher risks always. In order to eliminate such risks, you should provide transit encryption for your data.
When this is done, whenever the data will pass through untrustworthy, non-reliable and risky networks, it will be prevented from all kinds of interception and intrusion. Moreover, this is not at all a costly solution.
You can go with a digital certificate or HTTPS. Apart from this, it is vital to follow the latest updated security practices and standards. As and when they are made available incorporate them in your mobile app security checklist.
4. Security of API: Interlinked with mobile app security
Mobile app development and API are interconnected to a great extent. Any kind of risk to the security of any one of them hampers the other. Therefore, it is must to ensure high-end security of the API to attain a secure mobile app.
For this purpose, you should use only an authorized API in your app. Neglecting this can let hackers access your app’s information. Look at the illustration below.
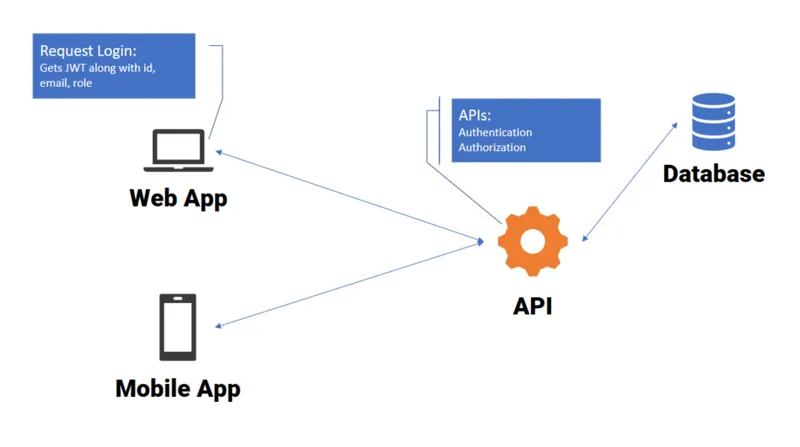
This is how APIs are used to transfer data between different parties. Therefore, any kind of security flaw in API can affect all the connected apps with it. Therefore, proper security rules have to be followed to ensure optimum security.
5. Give proper attention to consumer data protection
As discussed above, WhatsApp was under suspicion in recent times due to a threat to the personal information of its users. The most essential aspect of an app’s security is protecting consumer data.
Any hampering in this aspect can severely damage the reputation of the mobile application. Big brand names are capable of re-establishing the trust of consumers, but for smaller organizations, such flaws can result in a long term downfall of their business.
Therefore, no iOS or Android app development company cannot take any kind of risk in this case. With the advancement of technologies, certain introductions like biometric authentication have covered the risk concerned with customer data.
Moreover, the hot topic in the software technology world, blockchain is crossing all the limits to secure consumer data. The technology has decentralized ledgers which are uneditable to record the transaction.
Although crypto jacking is a new term introduced for the cryptocurrency hijacking. In this, the victim’s computer is infected with a virus that results in passive financial benefit. The renowned secure nature of the blockchain technology has been challenged with many cryptocurrency related crimes.
These cryptojacking crimes were on a continuous rise in 2018 and expected to increase in 2019. We can conclude that no solution is permanent to protect the customer data, so it requires constant research and development to ensure complete security of user’s data.

6. Testing software
Have you heard about the security flaws in the French government’s messaging app? The messaging app called Tchap was installed to protect official conversation within the French government from foreign entities, private companies, and hackers.
Elliot Alderson aka Robert Baptiste, who is known for exposing security flaws in popular applications has found out that although the service is restricted to the French government officials, he was able to make an account.
The bug in this top-notch python module has not been fixed since its discovery in July 2018. The app launched last month, that is, in April’ 2019. The government has said that a bug bounty program will be launched to identify other vulnerabilities.
Do you know where the chief problem lies? The problem lies in the testing of the application by companies providing native or hybrid app development services. You need a strong testing software to ensure complete security of your mobile application. You should not go for recently launched software for testing.
So, select a testing software that has been reviewed and advised by the majority as well as used by most of your competitors.
7. OWASP Standards: Ensure your mobile app do not violate them
Do you know how many mobile applications violate security standards? According to a report, 85% of the applications are not adhering to one or more standards of Open Web Application Security Project (OWASP).

This means that they are vulnerable to security flaws. In the same report, it was found out that there are serious issues in iOS app development as 30% of these apps use insecure HTTP and more than half of iOS apps do not use recommended secure encrypted communications ATS (Application Transport Security) method.
Similarly, 52% of Android apps had violated the standards which is more than iOS apps. This creates security problems in the long run after the launch. Therefore, make sure that your mobile application is not violating any of the OWASP standards.
A pro tip: Choose a feasible and practical security solution
Security needs of every mobile application are not the same. There is no such thing which can ensure the security of data for all types of applications. For instance, if you launch an app for an alarm clock, it has very fewer security vulnerabilities in comparison to an app for an e-wallet.
You need to figure out the security needs of your application after a detailed analysis and recommendations of security experts. Efficient Mobile app developers can help you with the security concerns related to your mobile application proficiently.
So, you should always contact with experts when it comes to security standards as a person with a non-technical background will never be able to stay well-versed with all the latest security trends.
If you have knowledge of any other latest update related to the mobile applications security vulnerabilities then please share with us in the comment section below.




